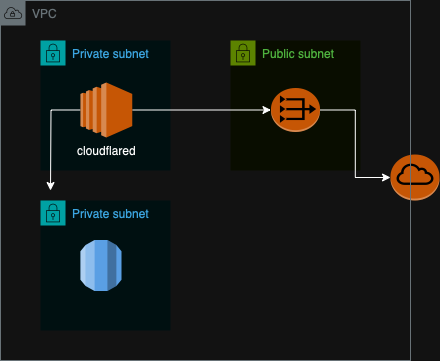
When designing infrastructure we should minimize the blast radius. We should be designing for isolation and segmentation and limiting ingress and egress. In an ideal state there will be no entrance. Nothing would be allowed in. So is it possible to design a network where this is possible?
The answer is, yes.
We can design a network that relies on egress only using a Secure Access Service Edge (SASE) architecture. This allows us to build a network where we can avoid all public exposure. Unlike a Virtual Private Network (VPN), the connectivity does not require a publicly accessible host.
Security should both affordable and accessible. Small businesses and startups should have access to this architecture without having to pay lots of money. Luckily, Cloudflare agrees with this. At the time of this writing, their Zero Trust product is free for small user bases.
In AWS, we set up a cloudflared tunnel in a private subnet to enable connectivity through Cloudflare’s WAN. Client machines install WARP for access. We create security groups to allow resources to respond to requests coming through the cloudflared tunnel. There is now connectivity without having anything exposed publicly. We can secure the cloudflared instance further by using Session Manager. This will remove any access path outside of the AWS Management Console.
By adding SASE, we’re creating defense-in-depth by adding another layer attackers now need to penetrate to access our networks. Attackers will no longer be able to directly attempt to probe or access public resources. The attacker will have to compromise a client host with WARP installed or directly compromise Cloudflare before attempting to gain access to resources. Both of those come with additional costs and risks to the attacker which will help make us more unattractive as targets.